Try Compass for free
Improve your developer experience, catalog all services, and increase software health.
Articles
Tutorials
Interactive Guides
DevSecOps Tools
The DevSecOp tools that secure DevOps workflows

Kev Zettler
Full Stack Web Developer
Despite the best efforts by software companies, security breaches still occur. Since 2000, an estimated 3.5 billion people saw their personal data stolen. Part of the problem is that as software applications grow in codebase scale and complexity, so do the surface areas for security vulnerabilities and exploits.
Plus, as more organizations adopt a DevOps approach, which automates and integrates the processes between software development and IT teams, traditional security tools are often no longer adequate. Developers today need to embed security measures into every stage of the development workflow. When it comes to security for DevOps workflows, this practice is referred to as DevSecOps.
What is DevSecOps?
DevSecOps is the practice of integrating security into a continuous integration, continuous delivery, and continuous deployment pipeline. By incorporating DevOps values into software security, security verification becomes an active, integrated part of the development process.
Much like DevOps, DevSecOps is an organizational and technical methodology that combines project management workflows with automated IT tools. DevSecOps integrates active security audits and security testing into agile development and DevOps workflows so that security is built into the product, rather than applied to a finished product.
To implement DevSecOps, teams should:
- Introduce security throughout the software development lifecycle in order to minimize vulnerabilities in software code.
- Ensure the entire DevOps team, including developers and operations teams, share responsibility for following security best practices.
- Enable automated security checks at each stage of software delivery by integrating security controls, tools, and processes into the DevOps workflow.
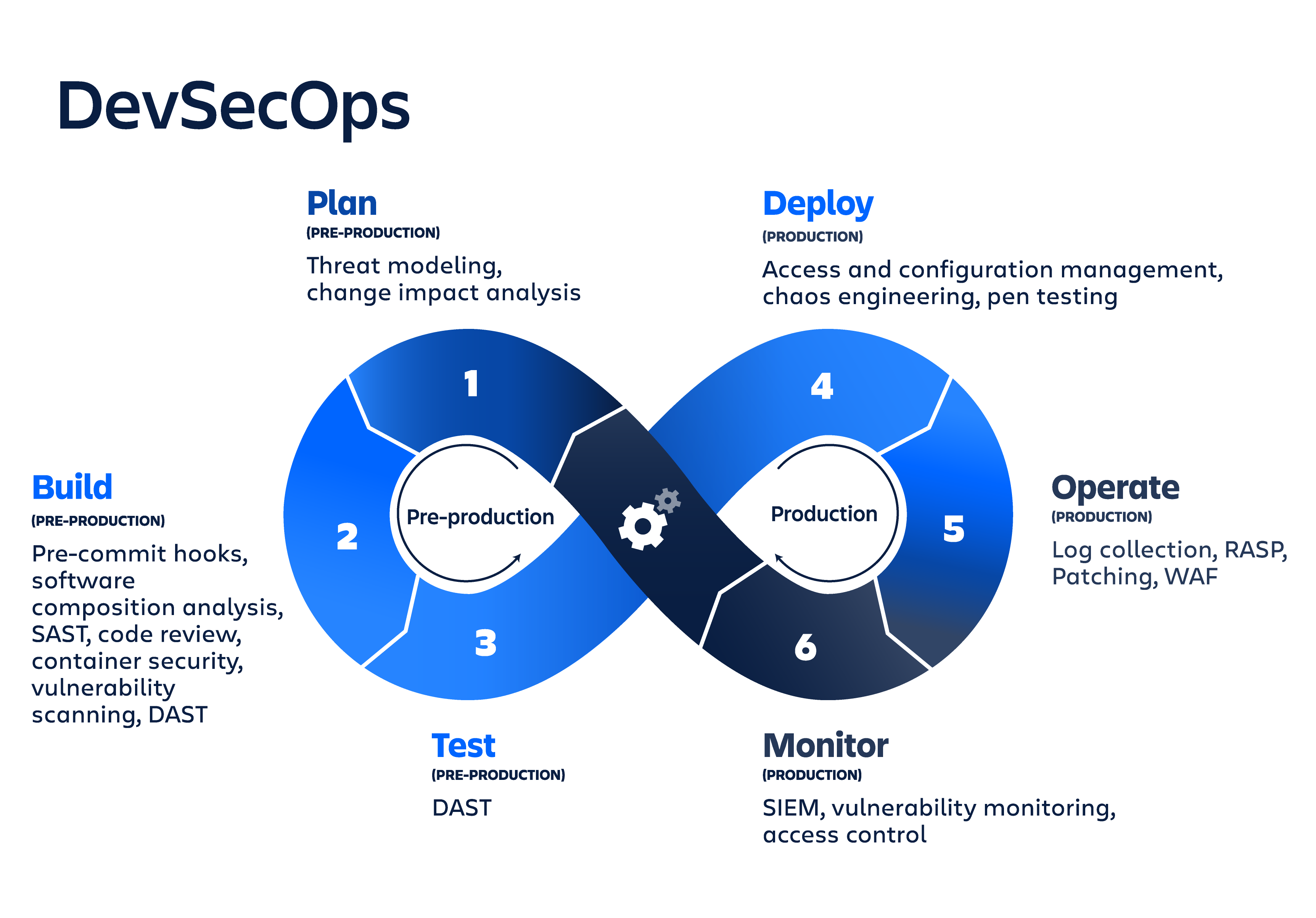
With DevSecOps, security should be applied to each phase of the typical DevOps pipeline: plan, build, test, deploy, operate, and observe.
Continuous is a differentiated characteristic of a DevOps pipeline. This includes continuous integration, continuous delivery/deployment (CI/CD), continuous feedback, and continuous operations. Instead of one-off tests or scheduled deployments, each function occurs on an ongoing basis.
related material
Learn more about Snyk for Bitbucket Cloud
See solution
Get Snyk for Bitbucket Cloud
Plan
The plan phase is the least automated phase of DevSecOps, involving collaboration, discussion, review, and strategy of security analysis. Teams should perform a security analysis and create a plan that outlines where, how, and when security testing will be done. A popular planning tool for DevSecOps is IriusRisk, a collaborative design tool for threat modeling. Additional tools include work tracking and management tools like Jira and communication and chat tools like Slack.
Build
The build phase begins once developers commit code to the source repository. DevSecOps build tools focus on automated security analysis against the build output artifact. Important security practices include software component analysis, static application software testing (SAST), and unit tests. Tools can be plugged into an existing CI/CD pipeline to automate these tests.
Developers regularly install and build upon third-party code dependencies, which may be from an unknown or untrusted source. External code dependencies may accidentally or maliciously include vulnerabilities and exploits. During the build phase, it is critical to review and scan these dependencies for any security vulnerabilities.
Some well-known tools to execute build phase analysis include: OWASP Dependency-Check, SonarQube, SourceClear, Retire.js, Checkmarx, and Snyk.
DevSecOps tools for the code phase help developers write more secure code. Important code-phase security practices include static code analysis, code reviews, and pre-commit hooks.
When security tools plug directly into developers' existing Git workflow, every commit and merge automatically triggers a security test or review. These tools support different programming languages and integrated development environments. Some of the more popular security code tools include Gerrit, Phabricator, SpotBugs, PMD, CheckStyle, and Find Security Bugs.
Test
The test phase is triggered after a build artifact is created and successfully deployed to staging or testing environments. A comprehensive test suite takes a considerable amount of time to execute. This phase should fail fast so that the more expensive test tasks are left for the end.
The test phase uses dynamic application security testing (DAST) tools to detect live application flows like user authentication, authorization, SQL injection, and API-related endpoints. The security-focused DAST analyzes an application against a list of known high-severity issues, such as those listed in the OWASP Top 10.
There are numerous open source and paid testing tools available, which offer a variety of functionality and support for language ecosystems, including BDD Automated Security Tests, JBroFuzz, Boofuzz, OWASP ZAP, Arachi, IBM AppScan, GAUNTLT, and SecApp suite.
Deploy
If the previous phases pass successfully, it's time to deploy the build artifact to production. The security areas of concern to address during the deploy phase are those that only happen against the live production system. For example, any differences in configuration between the production environment and the previous staging and development environments should be thoroughly reviewed. Production TLS and DRM certificates should be validated and reviewed for upcoming renewal.
The deploy phase is a good time for runtime verification tools like Osquery, Falco, and Tripwire, which extract information from a running system in order to determine whether it performs as expected. Organizations can also run chaos engineering principles by experimenting on a system to build confidence in the system’s capability to withstand turbulent conditions. Real-world events can be simulated, like servers that crash, hard drive failures, or severed network connections. Netflix is widely known for its Chaos Monkey tool, which exercises chaos engineering principles. Netflix also utilizes a Security Monkey tool that looks for violations or vulnerabilities in improperly configured infrastructure security groups and cuts any vulnerable servers.
By the release phase of the DevSecOps cycle, the application code and executable should already be thoroughly tested. The phase focuses on securing the runtime environment infrastructure by examining environment configuration values such as user access control, network firewall access, and secret data management.
The principle of least privilege (PoLP) is a key concern of the release phase. PoLP means that any user, program, or process, has minimum access to perform its function. This involves auditing API keys and access tokens so that the owners have limited access. Without this audit, an attacker may find a key that has access to unintended areas of the system.
Configuration management tools are a key ingredient for security in the release phase, since they provide visibility into the static configuration of a dynamic infrastructure. The system configuration can then be audited and reviewed. The configuration becomes immutable, and can only be updated through commits to a configuration management repository. Some popular configuration management tools include Ansible, Puppet, HashiCorp Terraform, Chef, and Docker.
The security community provides guidelines and recommendations on best practices for hardening your infrastructure, such as the Center for Internet Security (CIS) benchmarks and NIST configuration checklists.
Observe
Once an application is deployed and stabilized in a live production environment, additional security measures are required. Companies need to monitor and observe the live application for any attacks or leaks with automated security checks and security monitoring loops.
Runtime application self-protection (RASP) automatically identifies and blocks inbound security threats in real-time. RASP acts as a reverse proxy that observes incoming attacks and enables the application to reconfigure automatically without human intervention in response to explicit conditions.
A specialized internal or external team can perform penetration testing to find exploits or vulnerabilities by deliberately compromising a system. Another security technique is to offer a bug bounty program that pays external individuals who report security exploits and vulnerabilities.
Security monitoring uses analytics to instrument and monitor critical security-related metrics. For example, these tools flag requests to sensitive public endpoints, like user account access forms or database endpoints. Some examples of popular runtime defense tools include Imperva RASP, Alert Logic, and Halo.
In conclusion...
As more development teams evolve their processes and embrace new tools, they need to be diligent with security. DevSecOps is a cyclical process, and should be continuously iterated and applied to every new code deployment. Exploits and attackers are constantly evolving and it is important that modern software teams evolve as well.
A good place to start DevSecOps testing is to automate your testing with Bitbucket Pipelines. Also, be sure to review the test automation tools and resources available on the Atlassian Marketplace.
Share this article
Next Topic
Recommended reading
Bookmark these resources to learn about types of DevOps teams, or for ongoing updates about DevOps at Atlassian.

DevOps community
DevOps learning path