아티클
튜토리얼
대화형 가이드
Snyk Bitbucket Pipelines 통합으로 DevSecOps 달성

Simon Maple
Snyk의 현장 CTO
Bitbucket Pipelines 및 Jira에 Snyk를 통합하여 DevSecOps를 달성하세요.
시간
5분 분량.
대상 그룹
개발자, 보안/애플리케이션 팀 및 DevOps/DevSecOps 엔지니어입니다.
이 자습서에서는 Snyk를 사용하여 Bitbucket Pipelines 빌드 워크플로를 보호하는 방법을 간략하게 설명합니다. 환경 보안의 중요한 단계는 애플리케이션과 Linux 기반 컨테이너 프로젝트에서 알려진 취약점을 검사하고 분석하여 보안 취약점을 식별하고 완화하는 것입니다. 이 자습서의 연습에서는 Snyk Pipe for Bitbucket Pipelines를 활용하여 종속성에 대해 애플리케이션 매니페스트 파일과 컨테이너 기본 이미지를 검사하여 애플리케이션과 컨테이너를 보호할 수 있습니다.
Snyk 및 Bitbucket Cloud가 DevSecOps를 사용하는 방법은 애플리케이션 종속성에 중점을 둔 자습서입니다. 그러나 컨테이너 기본 이미지를 스캔하여 다음을 감지할 수 있습니다.
- 패키지 관리자가 설치 및 관리하는 운영 체제(OS) 패키지
- 키 바이너리 — 패키지 관리자를 통해 설치되지 않은 레이어
이러한 결과를 바탕으로 Snyk는 다음을 포함한 조언과 안내를 제공합니다.
- OS 패키지 및 키 바이너리 취약성의 유래
- 기본 이미지 업그레이드 세부 정보 또는 이미지 다시 빌드에 대한 권장 사항
- 영향을 받는 패키지가 도입된 Dockerfile 레이어
- 운영 체제의 고정 버전 및 키 바이너리 패키지
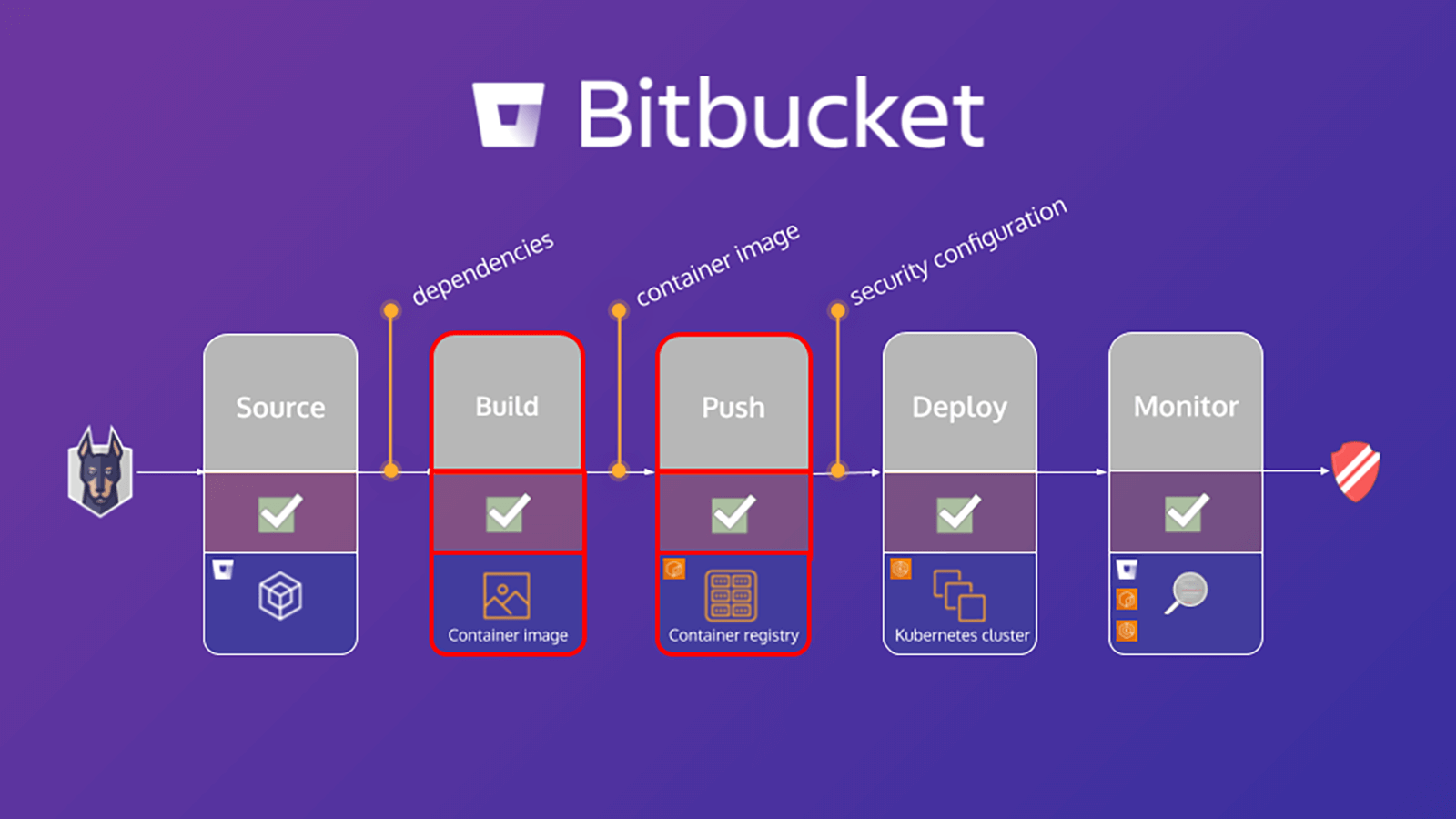
Bitbucket Pipeline에서 애플리케이션 스캔
bitbucket-pipelines.yml 파일은 Bitbucket Pipelines 빌드 구성을 정의합니다. Bitbucket Pipelines를 처음 사용하는 경우 시작하는 방법을 여기에서 자세히 알아볼 수 있습니다.
이 자습서에서는 워크플로에 매핑된 개별 단계가 포함된 샘플 bitbucket-pipelines.yml 파일을 제공합니다. 먼저 애플리케이션을 검사하고 Docker 이미지를 빌드한 다음 컨테이너 이미지를 검사합니다. 다음은 애플리케이션 검사 단계를 자세히 살펴보는 내용입니다.
scan-app: &scan-app
- step:
name: "Scan open source dependencies"
caches:
- node
script:
- pipe: snyk/snyk-scan:0.4.3
variables:
SNYK_TOKEN: $SNYK_TOKEN
LANGUAGE: "npm"
PROJECT_FOLDER: "app/goof"
TARGET_FILE: "package.json"
CODE_INSIGHTS_RESULTS: "true"
SEVERITY_THRESHOLD: "high"
DONT_BREAK_BUILD: "true"
MONITOR: "false"이 예에서는 파이프라인의 Snyk 스캔 파이프를 활용하여 애플리케이션 스캔을 수행합니다. 소스에는 지원되는 모든 변수에 대한 완전한 YAML 정의가 포함되어 있지만 이 코드 조각에 포함된 변수만 필요합니다.
그 중 몇 가지를 자세히 살펴보겠습니다.
1. SNYK_TOKEN은 이전에 [Bitbucket 구성] 모듈에 정의된 리포지토리 변수로서 파이프에 전달됩니다.
2. PROJECT_FOLDER는 프로젝트가 있는 폴더이며 일반적으로 기본 폴더입니다. 그러나 이 예제에서는 app/goof로 설정하고 이것을 파이프라인의 다른 단계에 아티팩트로 전달합니다.
3. CODE_INSIGHTS_RESULTS의 기본값은 false입니다. 하지만 여기서는 Snyk 코드 인사이트 보고서 테스트 결과를 만들려고 하므로 이 값을 true로 설정합니다.
4. SEVERITY_THRESHOLD는 제공된 수준과 같거나 더 높은 이슈를 보고합니다. 기본값은 low입니다. 그러나 이 경우에는 high에만 관심이 있으므로 이에 따라서 정의했습니다.
5. DONT_BREAK_BUILD의 기본값은 예상대로 false입니다. 정상적인 상황에서는 이슈가 발견되면 빌드를 중단하는 것이 좋습니다. 그러나 이 연습의 목적을 위해 true로 설정하세요.
Atlassian Marketplace의 새로운 Snyk Security Connect 앱을 사용하여 풀리퀘스트에 대해 Snyk 보안 검사를 실행하고 Code Insights에서 결과를 볼 수 있습니다. 쉽게 시작할 수 있으며 몇 번의 클릭만으로 앱을 설치할 수 있습니다.
컨테이너 이미지 검사
2022년까지 글로벌 조직의 75% 이상이 컨테이너화된 애플리케이션을 프로덕션 환경에서 실행할 것입니다(Gartner). 광범위한 채택과 함께 컨테이너 취약성이 급증했으며, 2018년에는 보고된 운영 체제 취약성이 4배 증가했습니다. 그러나 개발자의 80%는 개발 중에 컨테이너 이미지를 테스트하지 않는다고 말합니다. 자신의 책임이 아니라고 말하거나 다른 팀원이 이슈를 발견하는 데 익숙해져 있기 때문에, 빠르게 성장하는 비즈니스에서 컨테이너 보안을 확장하기 쉽지 않습니다.
파이프라인에서 컨테이너 이미지 검사
애플리케이션 검사에 대한 이전 섹션과 마찬가지로, 이 섹션에서는 bitbucket-pipelines.yml 파일을 구성하여 애플리케이션의 Docker 이미지를 빌드하고 이미지를 검사한 다음 해당 이미지를 레지스트리에 푸시하는 데 중점을 둡니다. 다음은 컨테이너 이미지 검사 단계를 자세히 살펴보는 내용입니다.
scan-push-image: &scan-push-image
- step:
name: "Scan and push container image"
services:
- docker
script:
- docker build -t $IMAGE ./app/goof/
- docker tag $IMAGE $IMAGE:${BITBUCKET_COMMIT}
- pipe: snyk/snyk-scan:0.4.3
variables:
SNYK_TOKEN: $SNYK_TOKEN
LANGUAGE: "docker"
IMAGE_NAME: $IMAGE
PROJECT_FOLDER: "app/goof"
TARGET_FILE: "Dockerfile"
CODE_INSIGHTS_RESULTS: "true"
SEVERITY_THRESHOLD: "high"
DONT_BREAK_BUILD: "true"
MONITOR: "false"컨테이너 이미지를 빌드하고 태그를 지정한 다음 파이프라인 Snyk 검사 파이프를 활용하여 컨테이너 이미지를 검사합니다. CODE_INSIGHTS_RESULTS, SEVERITY_THRESHOLD 및 DONT_BREAK_BUILD의 값을 같게 유지합니다. 또한 이 작업은 애플리케이션 검사 대신 컨테이너 이미지 검사에 대한 요청을 이해하기 위해 Snyk Pipe와 관련된 몇 가지 추가 지원 변수를 전달합니다. 즉, LANGUAGE를 docker로 설정하고, IMAGE_NAME을 선언하고, 적절한 리포지토리 변수를 전달하고, TARGET_FILE을 Dockerfile로 설정합니다.
이제 파이프라인이 컨테이너 이미지에서 알려진 취약점과 애플리케이션 코드를 검사합니다.
Atlassian Open DevOps에 대한 통합을 자세히 알아보세요
이 기사 공유
다음 주제
여러분께 도움을 드릴 자료를 추천합니다.
이러한 리소스에 책갈피를 지정하여 DevOps 팀의 유형에 대해 알아보거나 Atlassian에서 DevOps에 대한 지속적인 업데이트를 확인하세요.

DevOps 커뮤니티
DevOps 학습 경로