How to implement an Atlassian cloud IAM strategy
This four-part framework will help ensure your smooth transition to our identity and access management solution.
So, you’ve decided to move forward with cloud identity and asset management (IAM) for your organization. As you likely know already, managing user identity in the cloud is about more than implementing the right tools and mapping a migration path from your on-prem systems. You’ll also need to update your internal policies and make sure you’re set up to support ongoing growth.
We’ve been through our own digital transformation, so we’re equipped to offer these best practices to support your efforts as well. We mapped out a four-part framework that will help ensure your smooth transition to Atlassian cloud IAM.
Centralize management of cloud applications with a single source of truth
IT administrators transitioning to Atlassian cloud IAM will need to centralize the management of their cloud applications in one system, which will simplify a complex web of software products and instances and make it easier for IT teams to govern users across teams.
Cloud identity management looks different from managing identity on-premises. If your Atlassian products are used and managed on-premises, identity management looks like this:
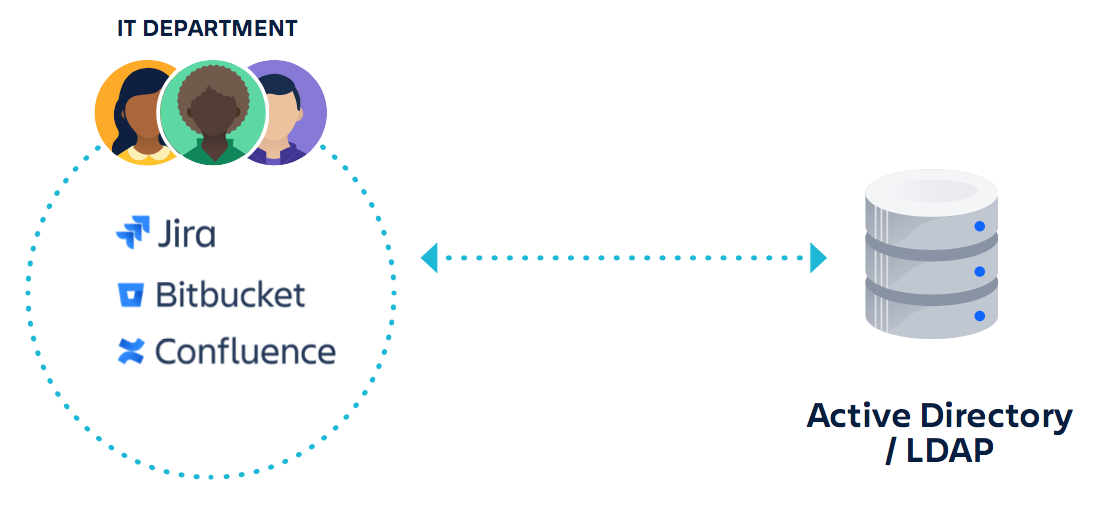
What you see here is one company’s instance of each product that is managed by the IT department and connects to your corporate Active Directory or LDAP directory.
But when users from multiple departments are accessing Atlassian and other cloud-based systems from multiple devices, their landscape looks more like this:
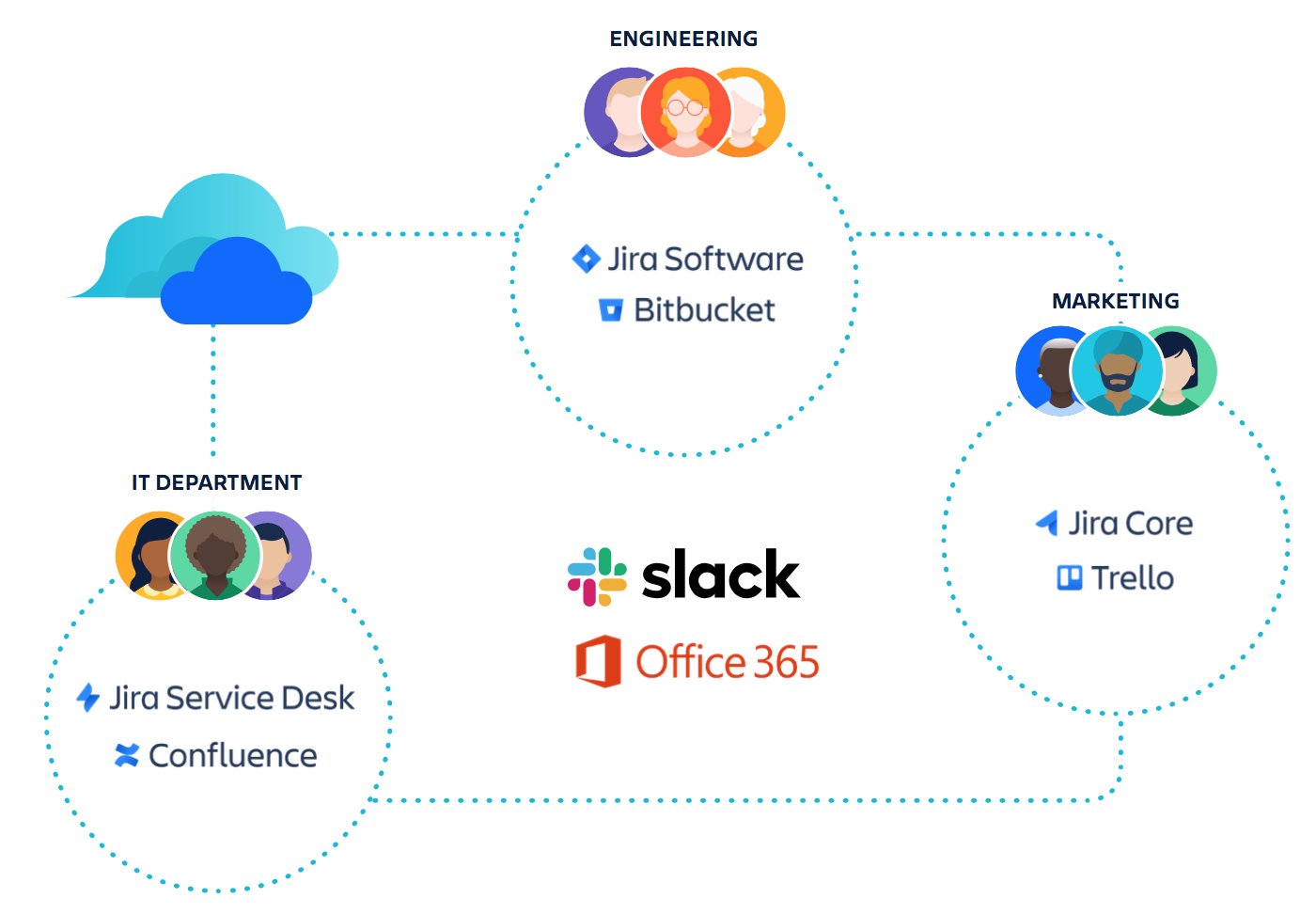
Here, multiple departments are using their own instances of cloud products, likely because each cloud subscription was purchased separately. The result is a web of solutions and accounts for IT to govern.
Atlassian cloud IAM makes it easy for IT teams to unravel this web by giving users one login, which corresponds to their email address. Regardless of what products, instances, or teams they’re part of, they’ll always sign in with the same credentials, making it much easier for administrators to manage their identity.
Organizations, the global administration layer for Atlassian cloud products, allows IT teams to manage multiple Atlassian cloud products and sites in one place.
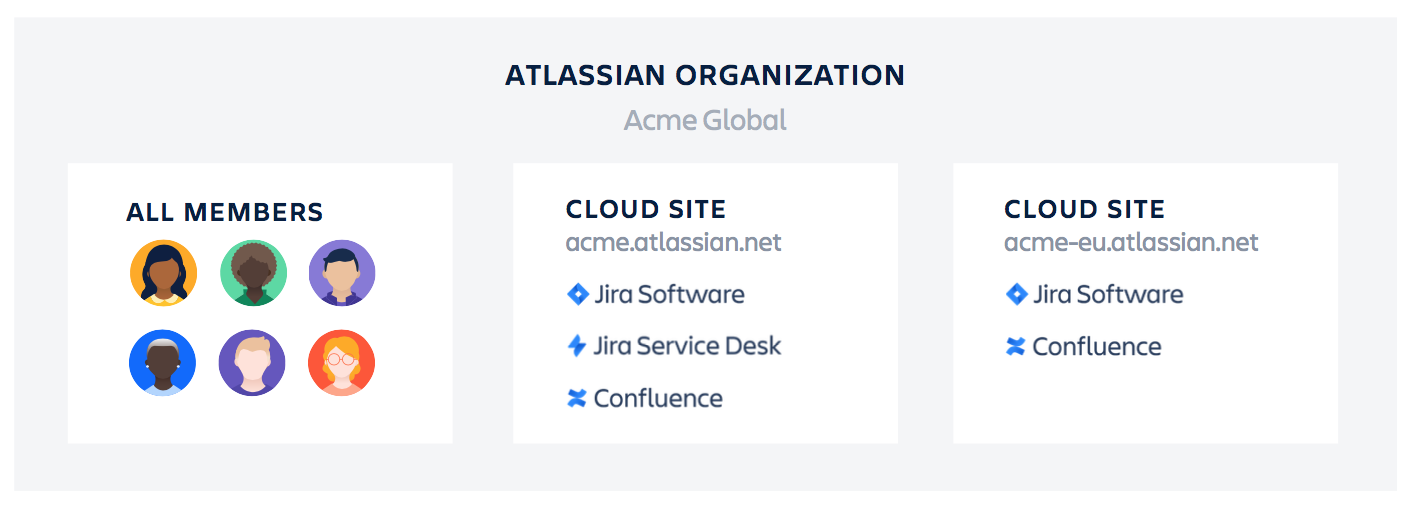
Sites contain instances of Atlassian cloud products, and each site can only have one instance of each product. An Organization brings all your Sites together, giving you a unified view of all the users of your company’s cloud apps. Within an Organization, you can manage all of your users across the cloud versions of Jira Software, Jira Service Desk, Jira Core, Confluence, Bitbucket, and Trello through a process called domain verification.
How does domain verification work? Once you verify the ownership of your domain, you can manage every user with an email address at your domain that Atlassian knows about. Atlassian refers to these as “managed accounts.” Organization administrators can export, change, deactivate, and delete managed accounts and enforce Atlassian Access security policies across them.
Integrate Atlassian with your identity provider
Integrating all of your applications with your primary identity provider will give your organization greater security and efficiency.
The most critical step in this process is enabling and enforcing SAML single sign-on (SSO) across all of your apps – not just your Atlassian cloud products. Your SSO provider allows you to ensure every user is meeting your requirements for strong passwords and multiple standards of authentication.
The most critical step… is enabling and enforcing SAML single sign-on (SSO) across all of your apps.
You can also use Atlassian Access to connect your Atlassian cloud products with identity providers for SSO, including custom SAML connections. Doing so helps you ensure all Atlassian product usage is going through an authentication endpoint that you manage.
As your company grows, you should also move from manual user provisioning to automated, policy-driven access management (or SCIM) through your identity provider. This transition will give IT a centralized view of the permissions assigned to each user and allow them to automate user provisioning and de-provisioning.
As a result, IT teams can automatically assign rules based on user or group attributes and provide product access only to those users who meet the requirements. Onboarding, off-boarding, and management of access and permissions can also be automated. That means that when an employee leaves the company, their access will automatically be removed, reducing the risk of data breaches.
Enforce security policies
Set up two-step verification and password policies if you haven’t already. Most identity providers manage multi-factor authentication, but if you don’t have an identity provider, you can use Atlassian Access to set up and enforce two-step verification.
Atlassian can also help you enforce password policies like password strength and expiry timeframes. Password strength can be set at five levels, ranging from weak to very strong, so IT teams can select different enforcement policies based on the unique needs of user subsets. Expiry time frames reduce idle session durations, so you can rest easy knowing your users aren’t leaving your data unattended.
Monitor user permissions and activities
IT teams should monitor changes in user access and permissions by auditing logs regularly.
Audit logs within Atlassian Access provide organization-wide visibility into user and group changes across your Jira and Confluence cloud products. These audit logs can tell you who made changes to permissions and who granted access. They also provide details on user and group memberships.
Our cloud access security broker (CASB) integration with McAfee also enhances visibility into activity across your organization’s cloud applications, including Atlassian cloud products. Together, these insights into your Atlassian Organization give you a comprehensive and documented view of who has access to your data, which can simplify investigations into changes and help prove compliance.
How to implement an Atlassian cloud IAM strategy
1. Create a plan that outlines your organization’s goals for growth, so you can prioritize requirements for your new IAM system.
2. Investigate identity providers (IdPs) and the identity and access landscape to determine the types of tools you’ll need.
3. Identify new or updated policies you’ll need to implement.
4. Choose your IdP and accompanying cloud applications to complete your IAM plan.
5. Create an Organization for your Atlassian cloud products and claim your domain.
6. Subscribe to Atlassian Access to apply security policies.
7. Integrate Atlassian Access with your identity provider for SSO and user provisioning.
Get set up with Atlassian Access
What’s next? Learn more about Atlassian Access, or give it a try free for 30 days.



