Our joint effort to further USAF Platform One
Atlassian and Ascend develop hardened containers for deployment to USAF Platform One.
Atlassian and Ascend Integrated are working together to further the Platform One initiative with the development, deployment, and support of security hardened Atlassian containers. Here, we’ll give a brief overview of United States Air Force (USAF) Platform One, provide details of the container hardening, deployment, and updating processes, and explain how agencies can take advantage of this mission-critical capability.
What is Platform One?
Platform One is a USAF DevOps and DevSecOps program focused on the build-out, deployment, and maintenance of containers using Docker, Kubernetes, and multiple security scanning tools. Containers are made up of applications for multiple USAF programs and projects, including the Atlassian tool suite.
Each container represents an application that has been verified, vetted, and validated to run in a cleared Authority to Operate (ATO) environment (on both the low and high side). Multiple USAF Programs use these containers to support program development and operations. Containers with applications can be retrieved from the DoD Centralized Artifact Repository (DCAR), or “Iron Bank.”
Container hardening and deployment
Atlassian and Ascend have been engaged with Platform One since the summer of 2019. Together, they’ve built and deployed hardened containers of Atlassian applications for retrieval from DCAR by DoD project teams.
The container hardening process incorporates three elements:
- Retrieving a base image of the operating system (generally RedHat or CENTOS based)
- Creating the Docker files with their associated Helm charts
- Justifying and remediating the Common Vulnerabilities and Exposures (CVEs)
The first step is pulling the base RedHat Linux operating system from the DCAR repository, which holds all images for Platform One. Combining this image, the Docker files, Helm charts, and the local version of Kubernetes (minikube), the container build is tested locally. If the build is successful, it’s submitted for review by the Platform One team, who runs the build through their CI/CD pipeline and provides Ascend with a scan file of all vulnerability results for the containers. The scanning tools in use are Anchore, Twistlock, and OpenSCAP.
Ascend built JetDock, a secure DevOps portal, specifically to aid this process, which is supported and sponsored by multiple Platform One contracts. JetDock automates the deployment of the containers by identifying updated application versions, containerizing applications, and processing the scan files, removing duplicates and previously cleared vulnerabilities. The screen below shows how JetDock organizes and grades the containers, along with a list of relevant CVEs.
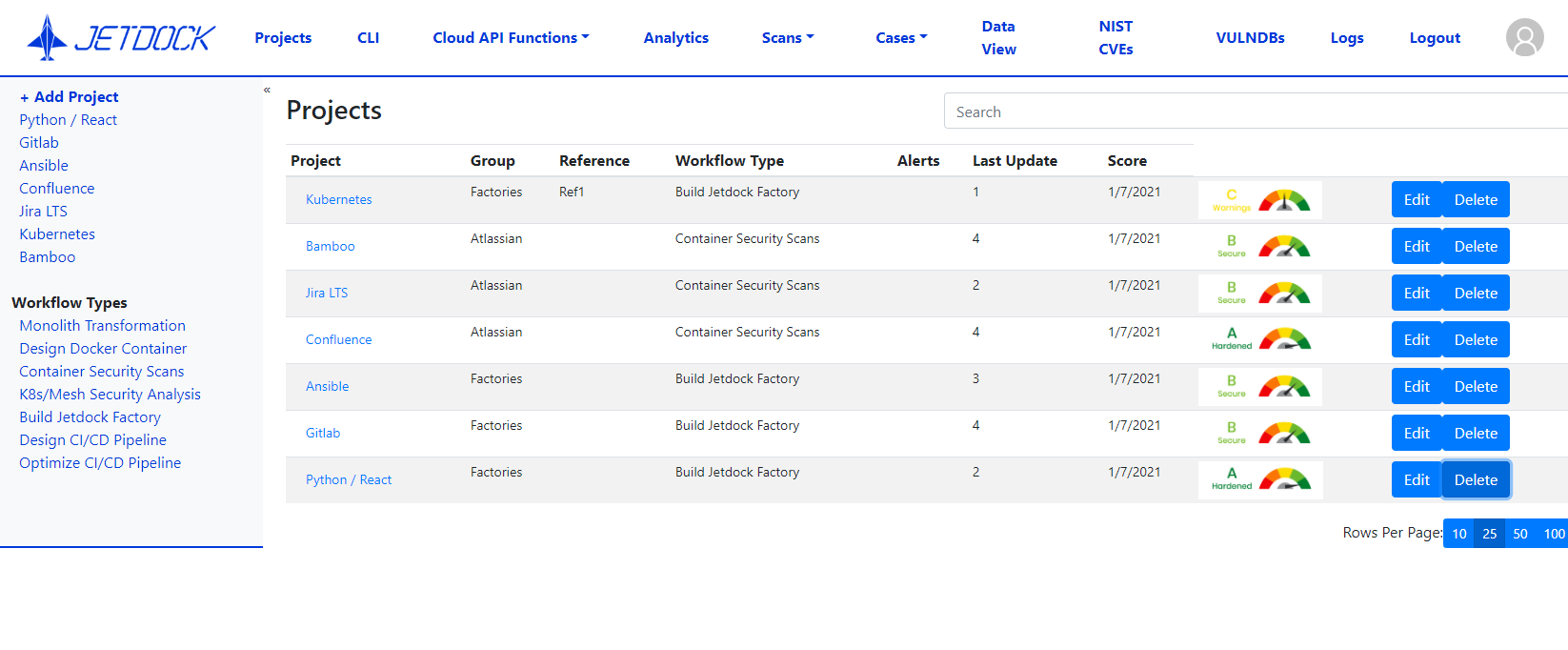
Following the vulnerability scan, JetDock removes false positives, including those not associated with Atlassian products or affecting different versions of the containers being deployed. The remaining list of vulnerabilities is passed to Atlassian for analysis, and then sent to the Platform One Approval Committee for review and certification.
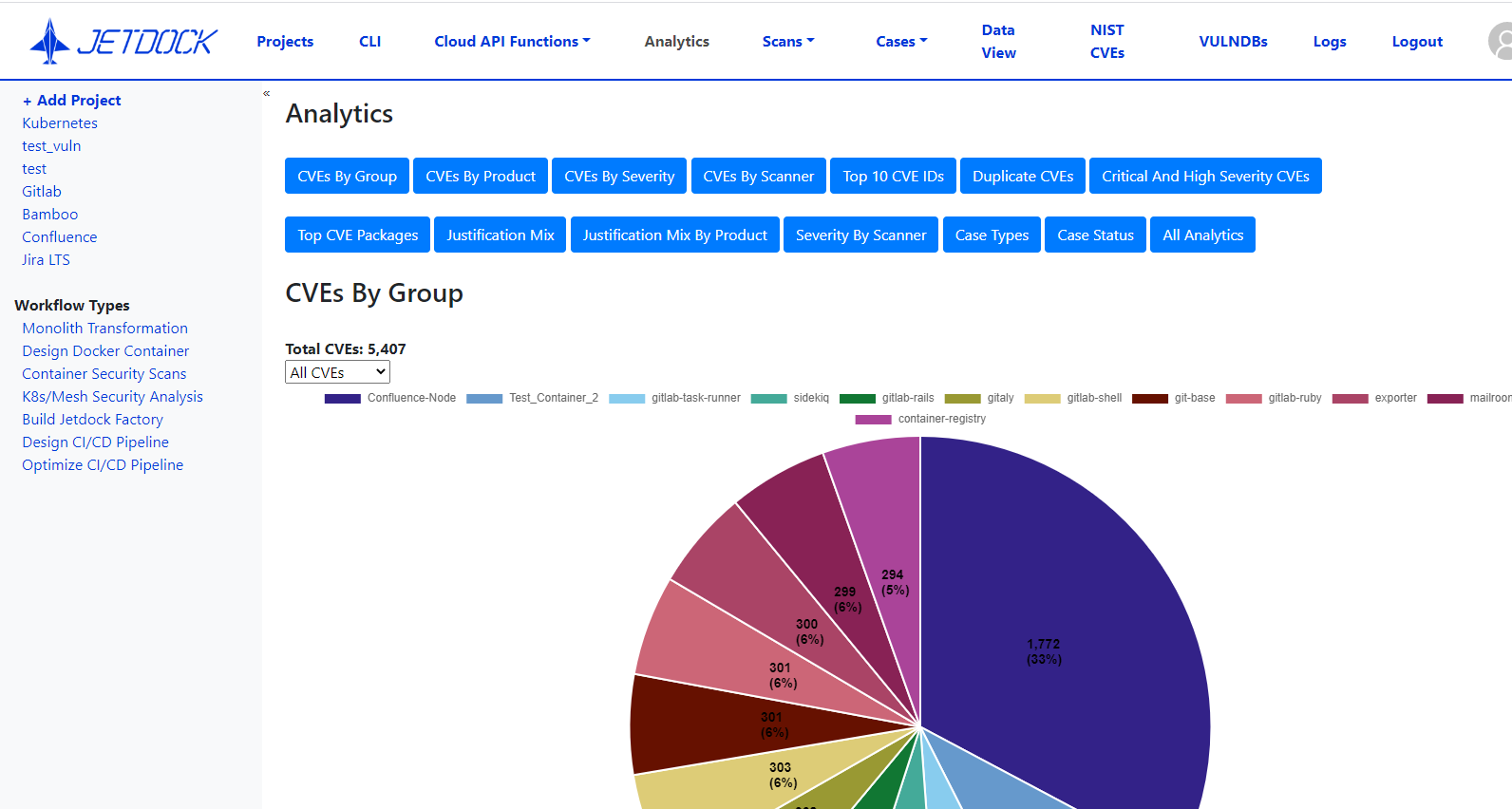
Once a container is approved by the committee, any DoD agency or department can pull the image from DCAR and use the application in their own environments. JetDock also generates overall reports about container usage, application versions, and any vulnerabilities that have been identified.
Keeping the containers updated
Containers hosted within the DCAR “Iron Bank” need to be regularly updated to ensure that hosted applications are kept current with security and functionality updates. JetDock keeps an eye on public repositories to see when a new version of an Atlassian tool has been released. When a new release is detected, JetDock updates the Dockerfile with the new version and builds a container with the latest DoD-approved OS.
When the container is built successfully, it is tested on Kubernetes to ensure that the Helm charts for deployment work, and that any necessary adjustments are made. Once the automated tests are passed, JetDock checks the Dockerfile into the DCAR Git repository. After the Platform One team returns the Excel spreadsheet with vulnerability scan results, JetDock adds it into the case management system.
JetDock then reconciles any security findings with previously answered/justified/closed issues, suggests possible justifications for new scan findings, and provides a list of findings that require human attention. New justifications are stored for future automated scans.
How agencies can get started
Leveraging Atlassian containers for Jira, Confluence, Bitbucket, and Bamboo is a simple process, and these powerful DevSecOps tools are now available on Platform One’s five-year, $95M Basic Ordering Agreement (BOA) 2 for DevSecOps Tools, Platform Integration, and Licensing. Teams can purchase, upgrade, or renew their current licenses through the program, and support, services, and expertise surrounding the Atlassian product stack are also available.
This BOA was awarded to several Atlassian partners. Their intent is to provide government departments and agencies with an accelerated path to a vetted contractor pool. Leveraging the BOAs eliminates the need for individual defense program offices to conduct additional market research, and has been shown to cut the total acquisition time by over 75 percent.
Ascend provides ongoing support to the build-out, deployment, and maintenance of containers hosted in the DCAR environment. Funding of the JetDock application and the award of a new multi-year contract supporting Platform One ensures the continuing development and streamlining of the process between DoD, Atlassian, and Ascend. The availability of hardened containers for Atlassian tools accelerates the DoD’s move to secure, innovative code development with a diverse range of DevSecOps-as-a-service environments for all types of systems. For more information, contact us at govsales@atlassian.com.
