Enhancing security in Bitbucket: Introducing expiry for access tokens
As part of Atlassian’s ongoing investment in security, we’re introducing new controls to help administrators manage authentication tokens more effectively and securely. To reduce the risk of long-lived credentials becoming security vulnerabilities, all newly created access tokens in Bitbucket will require an expiry duration, as determined by the workplace admin.
Why are we making this change?
Previously, access tokens in Bitbucket Cloud could remain active indefinitely unless manually revoked, increasing the risk of unauthorized access. Organizations need stronger security controls to ensure credentials do not remain valid indefinitely and become potential attack vectors.
Requiring access tokens to have an expiry duration will ensure regular token rotation, reducing the risks of data breaches and helping organizations strengthen their security posture.
What’s changing?
Flexible token management: When creating a new access token at the workspace, project, or repository level, users must set an expiration date that adheres to the admin-defined limit (the default maximum is 365 days, unless modified by the admin). This expiration policy is applied consistently across all levels, ensuring transparency and streamlined credential management.
Admin controls: Workspace admins can enforce token expiration policies to align with their organization’s security requirements. Available options include 90, 180, or 365 days, with an option to allow tokens without an expiry if needed.
Mandatory expiration: Users must set an expiration when creating access tokens, choosing a duration within the limits set by workspace admins. If “No expiry” is allowed under the policy, users may select that option. Users will not be able to choose an expiration outside the admin-defined policy, as any options beyond the allowed range will be disabled.
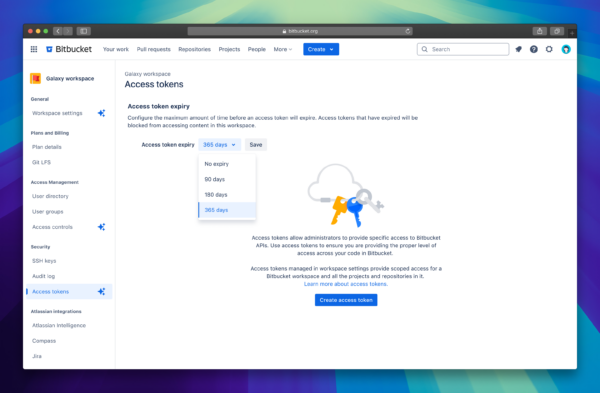
How to configure access token expiry
- Workspace admins navigate to Workspace settings > Access tokens.
- Under Access token expiry, choose from the available expiration options: 90, 180, or 365 days, or allow No expiry if required (default maximum is 365 days).
- Save your changes—this policy will apply to all newly created tokens in your workspace, project, and repository.
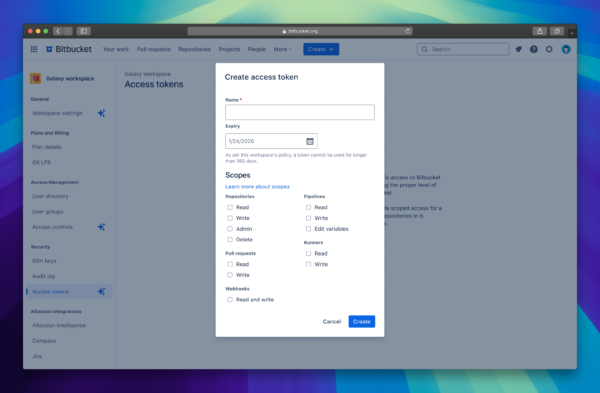
How to create an access token with expiry
- Go to Workspace, Project, or Repository settings (depending on where you are creating an access token) > Access tokens.
- Click Create access token.
- Select an expiration period that aligns with the maximum allowed by your administrator (default maximum is 365 days).
- Generate and securely store your token. Expiration details will be visible in the access tokens list.
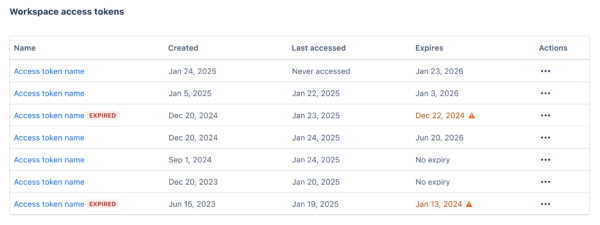
What’s next?
This update is part of a broader effort to strengthen Bitbucket Cloud’s security and customers enhance their overall security framework. Looking ahead, we’re exploring additional enhancements, including token rotation mechanisms and expanded security controls for other authentication methods.
For more details, check out our access token support documentation.