Most enterprises used to structure their cybersecurity as a monolithic, imposing wall around their organization – an approach often called “castle-and-moat security.” On-premises controls were designed to protect everything within the organization’s network – all users, devices, and apps that made it past a firewall were trusted by default. Employees outside office walls could connect via virtual private network (VPN), essentially building a secure bridge into the corporate network.
In today’s cloud-first world, however, a castle-and-moat security strategy can no longer protect an organization’s crown jewel: its data. Ninety percent of today’s companies have moved away from a purely on-premise setup, with employees accessing corporate data from multiple unsecured mobile devices and dozens of apps. Organizational data no longer lives solely within on-premises computers protected by a firewall. This shift has enabled a mobile, distributed workforce, but has also provided nefarious actors multiple entryways into an organization, through app data breaches, credential theft, or risky networks.
Fortunately, there’s a fresh approach to enterprise security for perimeterless workplaces. The Zero Trust security model, embraced by industry experts worldwide, replaces the single-perimeter security approach with one that continuously verifies individual users’, devices’, and assets’ security, regardless of what network they’re joining from. It ensures safe, mobile, and flexible cloud security, allowing enterprises to scale in the cloud without compromising their shifting borders.
Zero Trust security: a modern solution to modern risks
If castle-and-moat security is analogous to fortresses of ages past, you can think of Zero Trust as the approach a modern castle-turned-museum might take to security. Filled with valuable objects, a historical site today might check your identification and have security keep an eye on visitors as they roam the castle. Strategically placed cameras would capture any wrongdoing that guards might miss in real time.
That’s precisely how Zero Trust works. Eschewing the idea of protecting corporate data with a single security perimeter, it instead ensures security at the user level by continuously authenticating users’ credentials and devices and limiting their access to information. Admins can embrace a Zero Trust model by implementing flexible identity and authorization measures, setting up trusted devices, and laying out granular access controls to protect sensitive data.
The principles of Zero Trust security are:
- Never trust; always verify. Just like a security guard might ask for ID, Zero Trust relies on verifying all users. Organizations can’t control every IP address or device that accesses their data, so they can’t assume trust within their network perimeter. Those building a Zero Trust architecture shouldn’t inherently trust anything on or off their network.
- Grant access based only on users’ authenticated identity and device, regardless of their network location. Whether they’re logging in from the office or a coffee shop, Zero Trust asks users to authenticate their identity so that you can confirm who they are and that they have access to a certain resource.
- Access controls should be dynamic and continuously verified. Zero Trust requires routine authorization checks to ensure no risks slip through the cracks.
Currently using Atlassian on-premise products?
Learn how to migrate to Atlassian Cloud and take advantage of industry best security practices.
How to build a flexible Zero Trust security strategy
A solid Zero Trust strategy is built on the approach’s primary principles. To get started, look at your identity and authentication settings, device verification process, and access management controls.
Set up strong user identity and authentication processes
Continuous identity verification lies at the heart of a Zero Trust security strategy. To make sure employees have the right access to the right resources, you’ll need to have a robust user management system in place and set up strong processes.
To start, make sure your employees’ user identity is centralized in a group directory or user database. Ideally, your user directory should be synced to your HR processes so that any changes made to a user’s employment, role, or team are reflected in your user database. That way, if an employee’s move between departments or departure from the company is logged in your user directory, their access to resources will automatically be updated or rescinded.
Within Atlassian Cloud, you can build out this database by syncing an external identity provider—such as Okta, OneLogin, Google Cloud, or Azure AD—to Atlassian Access. Once your user database is synced through Atlassian access, you can set up security measures such as single sign-on (SSO), allowing users to authenticate into multiple Atlassian cloud tools by logging in just once. SSO will validate users against your group directory and, if their identity is confirmed, give them time-limited use of the resources they have access to.
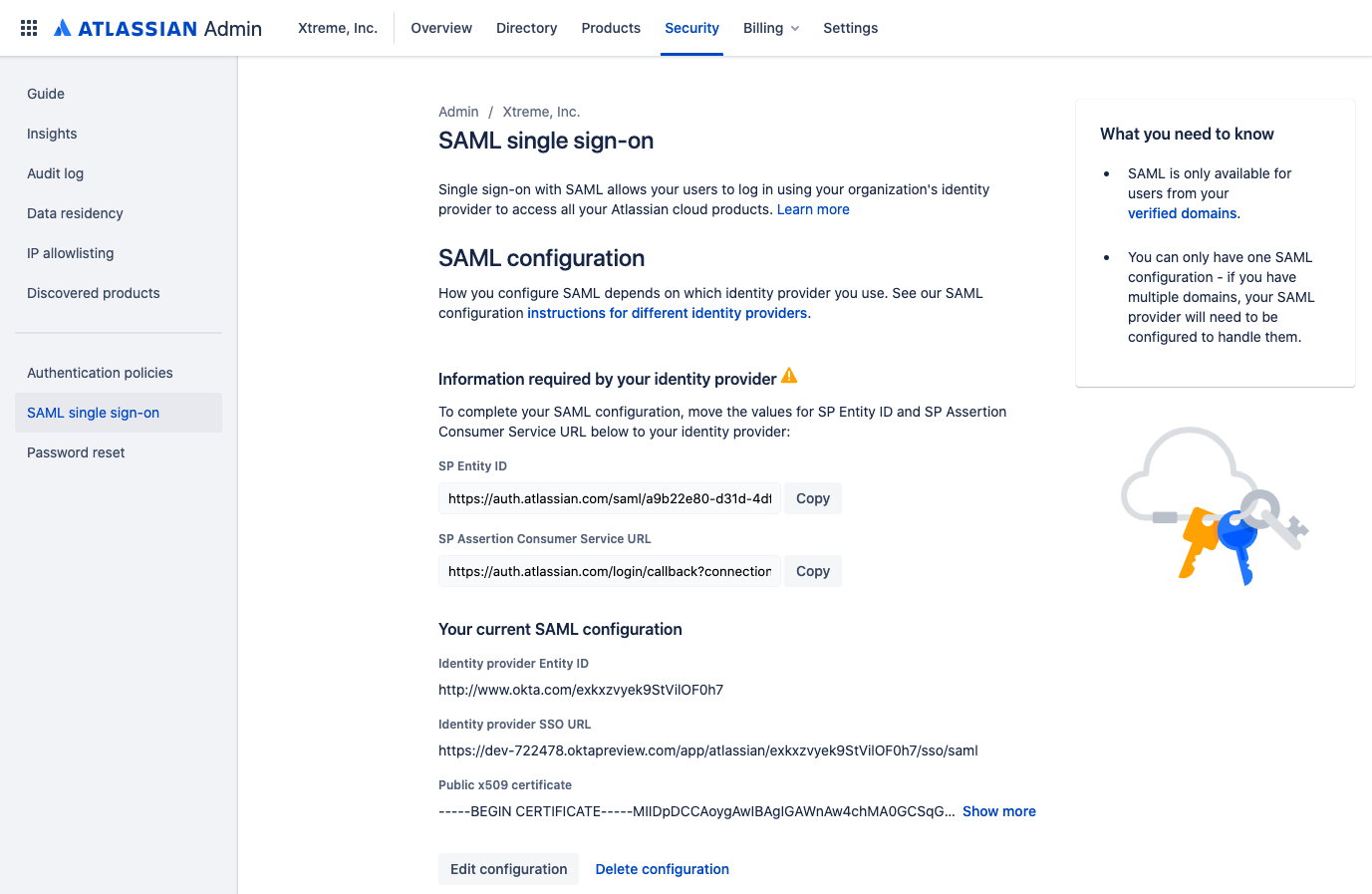
With a user database in place, you can also choose to double down on verification measures. Within Atlassian Access, for instance, admins can enforce multi-factor authentication—requiring users to authenticate in two distinct ways before they gain access to any corporate systems. By having users verify their identity through a second step (usually with a code sent to a separate device), you can ensure your users are who they say they are—even if their passwords have been compromised or their devices have been stolen.
Authenticate devices
Once you’ve made sure you can easily identify and authenticate your users, their devices are next. Because while your user verification processes may have proven your employee is indeed on the other end of your log-in screen, their device presents its own security risks. Unverified endpoints—such as employees’ personal mobile phones—might access risky networks, frequently switch access between corporate and personal data, or be lost by their owners. That’s why Zero Trust also confirms device ownership and devices’ compliance with corporate security measures.
In a Zero Trust model, devices accessing corporate data should be uniquely identified in a database, such as Atlassian’s mobile device management (MDM) program. By having employees register any bring-your-own-device (BYOD) and corporate devices in an MDM program, you’ll know exactly which devices are accessing your system and ensure that they meet your enterprise’s security needs (by having up-to-date operating systems or requiring a passcode).
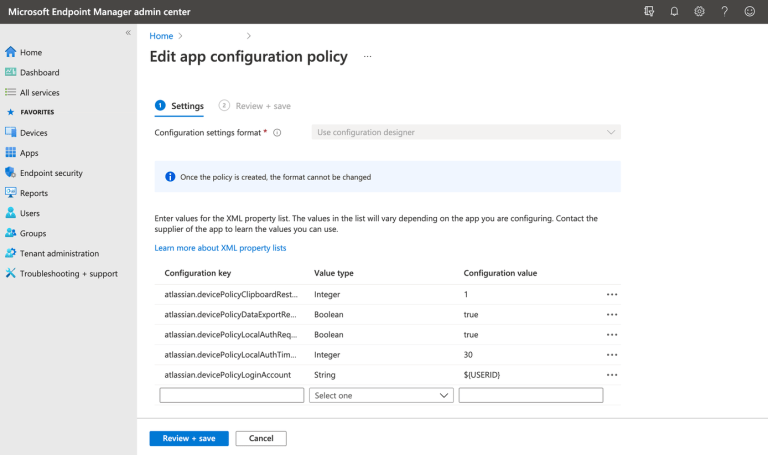
Yet, even with most employee devices registered in an MDM program, not all devices present the same level of risk to an organization.
To decide which types of devices can access certain platforms, you first need to identify the risk associated with each platform or app to which you’re granting users access. At Atlassian, for instance, we do this by tier—categorizing a platform’s risk by the sensitivity or confidentiality of the data it stores. Depending on a platform’s sensitivity, we make it available at an open, low, or high tier of security. Each of those tiers then requires different levels of user and device authentication:
- Open-tier platforms can be accessed through successful user authentication into Atlassian’s network, regardless of the device. Apps in this tier don’t store any personally identifiable information (PII), user-generated content (UGC), or intellectual property (IP).
- Low-tier platforms require both user authorization and the use of a trusted corporate device (whether it’s Atlassian-issued or a BYOD enrolled in our mobile device management program). Devices must have up-to-date operating systems, be protected by passwords, and have local drive encryption. Apps in this tier can store staff PII and be used for basic collaboration (such as chatting or emailing), but they can’t store UGC, acquire payment information, or provide access to customer-facing systems.
- High-tier platforms require user verification and can only be accessed on Atlassian-issued corporate devices—no BYOD allowed. Apps in this tier can store UGC, process payment information, and have privileged access to customer-facing systems.
Put an access management system in place
Once you have solid systems in place to verify both users and devices, it’s time to define your policies around who can access certain tools and pieces of data. The Zero Trust approach is built on the idea that employees should only be given the minimum access they need to do their job effectively—and no more. That way, even if an attacker gains access to—for example—a junior software engineer’s credentials, the intruder won’t be able to access confidential data from the finance, HR, or marketing departments. The damage they can do is limited.
To manage access in this way, you’ll need to define exactly which resources different employees need access to. You can generally do this by role, mapping out the tools and assets each type of user requires. Using an identity provider, you can then leverage user provisioning to automatically grant certain groups access to specific tools and data without giving them access to all of the apps your organization uses.
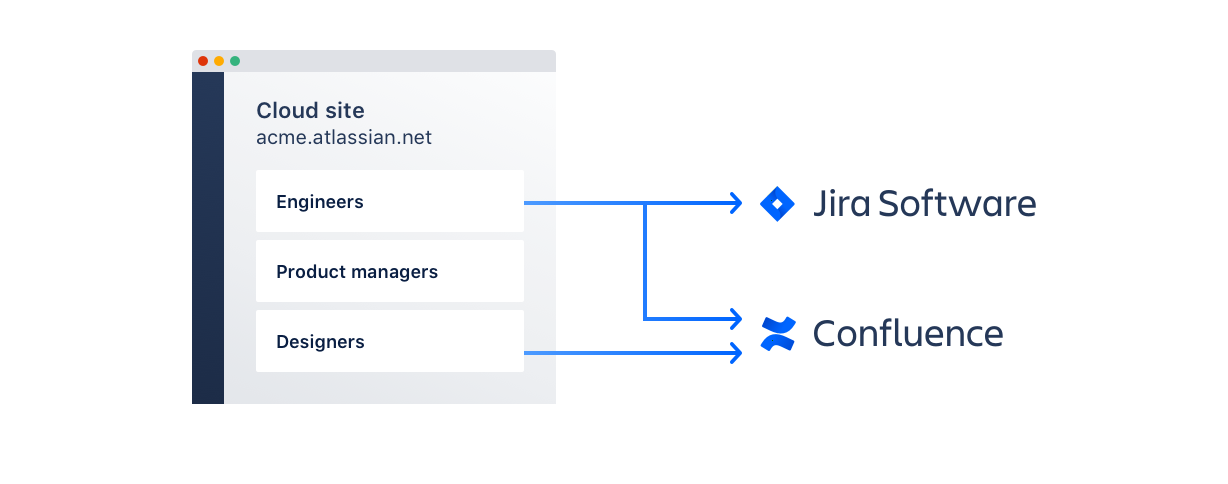
With Atlassian Access’s user provisioning, you can set up different groups of users and provide them with access to precisely the tools needed to do their job. New employees simply need to be added to a group, and they will receive permissions to the tools they require. If employees change departments, simply reassign them in your identity provider, and they will gain secure access to the apps they now need—while losing access to any systems they no longer require.
Through Atlassian Access, you can also set multiple authentication policies, customizing security settings as needed for different subsets of users. This allows you to create unique authentication policies for user subsets depending on the sensitivity of the information being accessed and the risk introduced by the users accessing said data.
Of course, even with a solid access management system in place, you should still monitor for any suspicious activity—just like our castle-turned-museum would have cameras installed in case guards missed any funny business. Make sure admins have privileged access to your organization’s audit logs, where they can monitor historical user, group, and product access information across your applications. If you work with a Cloud Access Security Broker (CASB), you can also sync it to Atlassian Access, allowing you to track and analyze all information sent by your Atlassian Cloud products and giving admins greater visibility into content and user interactions.
Start applying Zero Trust security practices
Defining and implementing Zero Trust security isn’t easy – but with the risks involved in the cloud, the benefits are worth the setup time. According to IBM, the average cost of enterprise data breaches today is $3.86 million. By adopting Zero Trust, you can help protect your modern enterprise from modern security risks.
Learn more about how you can set up the perfect security model for your enterprise with Atlassian Access, or dive deeper into understanding Zero Trust security by reading our guide.